
Rise of Phishing-as-a-Service (PhaaS)
Selina CoenWhy Strong Phishing Protection Matters More Than Ever with the Rise of Phishing-as-a-Service (PhaaS)
Email spoofing is the creation of emails with a forged sender address in order to trick the recipient into providing money or sensitive information. If your organization uses a registered domain for their email, then chances are you have seen some of these in your inbox. It's also likely that most, if not all, were simply a phishing scam.
The initial fear in these circumstances is that the sender account has been hacked. If your own account were compromised, an attacker could use it to implement social media attacks against your fellow employees and email contacts. At the least, it could be used as a spamming account, which would negatively affect your email reputation. The good news is that email accounts are rarely hacked. Most of these occurrences are due to email spoofing.
Spoofing is all about making it appear that the email is coming from a sender that you trust, including yourself. In actuality, the email originated from an external source that could be on the other side of the world. Unfortunately, it is easy to spoof an email account today. Any email server can be configured to send mail from any given domain for someone with the required knowledge. Even if you don’t have the equipment or know-how, there are websites that will let you send one-off emails using the email address of your choice. All of this is possible because the email protocol makes spoofing possible by its very design. That’s because security was not built-in to the email protocol when it was created.
Sign up for a FREE Demo of SpamTitan and learn how it works to stop email spoofing.
Book Free DemoA good rule today for emails that ask you to “do something” is to not just rely on the Display Name. For instance, the sender name may be PayPal but the email address is paypal@eydh12.com. If an email is coming from a trusted source within your company, a quick glance down at their email signature may be a clear indication that the email didn’t come from that person. Spoofed email signature often contain bogus phone numbers that have no correlation with your company or lack the mandatory company logo. You can also click the forward button which will then show the “To” and “From” fields of the original email in the body.
While verifying the correct email address will allow you to properly discern if an email has been spoofed a majority of the time, it isn’t foolproof. The only way to absolutely know where an email came from is to examine the email header. Each email application has a different way to access the header.
There is a lot of information contained within the email header, far more than you want to probably know about. When you read an email header, the data is in reverse chronological order. This means that the information contained at the top is the most recent. In order to trace the email from sender to recipient, you need to start at the bottom. There are two very important fields contained in the full header.
Received:
This part of the header lists all of the servers and computers that were utilized to send the email. Because we go from the bottom up, the last “Received:” line is where the email originated. This email domain should match the one being displayed in the email.
Received-SPF:
The Sender Policy Framework (SPF) is used by organizations to specify which servers are permitted to send email on its behalf. Mail sent from permitted servers will show up as “Pass” in the Received-SPF field, which is a very strong indicator that the email is legitimate. If the results show “Fail” or “Softfail”, that’s an indication that the email may be spoofed. Keep in mind that this isn’t true 100 percent of the time as some domains don’t keep their SPF records up to date, resulting in validation failures.
Optional Fields:
For those organizations that choose to utilize DKIM and DMARC, the header has one more field to give clues:
Authentication-Results:
This field will let you know if the email passed DKIM or DMARC authentication. While SPF can be bypassed by spoofing, DKIM and DMARC are far more dependable.
Email filters using the latest anti-malware security features is the primary way administrators can block these attacks, getting to the root of the issue – phishing emails. Blocking phishing emails stops users from clicking malicious links, so an administrator does not need to limit file sharing functionality. Instead, the administrator can stop the attack before it ever reaches the user’s inbox.
Protect your business from phishing threats with SpamTitan email security. Learn how it works.
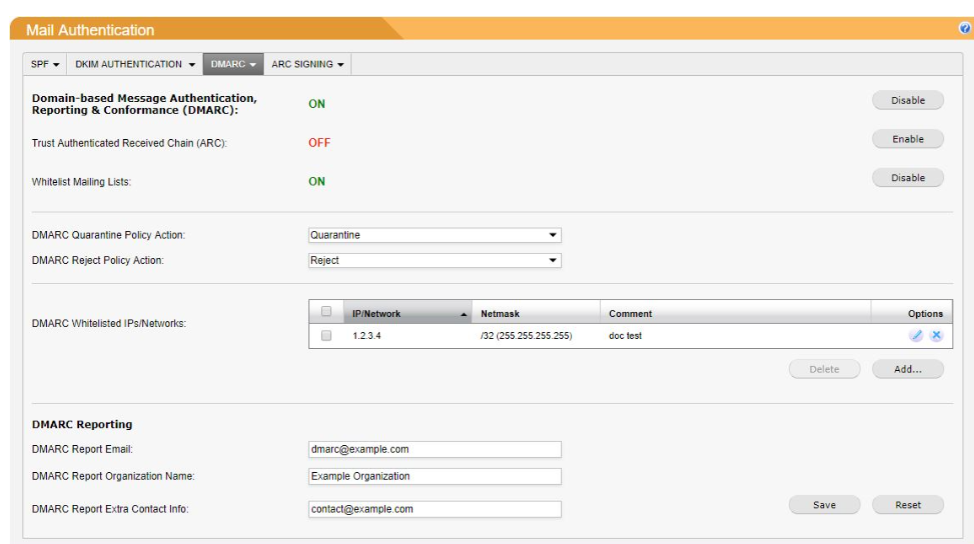
Book Free DemoDMARC (Domain-based Message Authentication, Reporting, and Conformance) defenses stop phishing emails based on administrator settings and a set of rules that leverage DNS and public-private key encryption. It incorporates Sender Policy Framework (SPF), which requires a DNS entry from the organization so that recipient email servers can identify if the sender’s IP is authorized to send an email on behalf of the domain owner.
DomainKeys Identified Mail (DKIM) is also incorporated into DMARC rules. DKIM adds a public-key encryption signature that can only be decrypted by the organization’s email server that contains the private key. By adding a signature to the email message, the organization knows that only messages encrypted with its public key are intended for the recipient. Together with SPF, this security framework blocks spoofed messages that might look like they came from a trusted sender.
OAuth attacks are common in the wild, and it only takes one user mistake to give an attacker access to a cloud drive. With DMARC and the right email filters, an organization can stop an attacker from ever reaching a targeted user’s inbox.
Related Article fror you - Enabling and Configuring DMARC in SpamTitan
The risks from spoofed and malicious emails are much greater today. Individuals can lose financial security due to identity theft. Organizations’ databases can be mined for social security numbers, credit card information, health records, bank account numbers, etc. leading to billions of dollars in damages to, not only the organization, but also the people whose information has been stolen. Small businesses are often the victim of significant financial damage caused by malicious emails. We usually don’t hear as much about these as we do the large Targets, Sonys and Homebases of this world.
Despite the fact that it’s relatively easy to protect against spoofed emails it’s still a common technique used by spammers and cyber-criminals. It does take some effort, and therefore money, to combat email spoofing. I suspect that is why many small companies do not take the necessary precautions. My recommendation to my clients is pretty straightforward:
Email is a necessary and extremely useful business communication tool. Unfortunately, because it's used so much it makes an easy target for cyber-criminals. For an average email user it’s a difficult task at best to spot a malicious email among the hundreds or thousands that pour into their inbox. That is why it's so important for organizations to allocate the resources and funds to protect their personnel and their organization from all the threats that may arrive as an innocent looking message from a friend.
Since 1999 SpamTitan has been building threat intelligence to dramatically reduce the risk of a successful attack on your organization. With SpamTitan you’ll significantly reduce the risk of new variants of malicious email from entering your network.
If you are looking for the best spam filter for business users, check out SpamTitan – the leading anti-spam solution for SMBs, MSPs and Schools.
Protect your business from spoofing emails. Sign up for a FREE Demo of SpamTitan today.
Book Free Demo
Why Strong Phishing Protection Matters More Than Ever with the Rise of Phishing-as-a-Service (PhaaS)

Deepfakes are becoming increasingly realistic and accessible, posing serious cybersecurity and reputational risks for businesses. Learn how they work, the threats they pose, and what IT teams can do to...

Explore the critical importance of robust email security in 2025. Learn how advanced threats like phishing and business email compromise are evolving, and discover strategies to protect your organization effectively.
Sign-up for email updates...

Call us on USA +1 813 304 2544 or IRL +353 91 545555
Contact Us