There have been many research studies into the success rate of phishing; the statistics vary, but they all agree that it is the most utilized method to begin a cyber-attack against an organization. The latest research from Symantec shows that 96% of data breaches start with a phishing email; 1 in 4,200 emails during 2020 was phishing email. Further research from Verizon's 2021 Data Breach Investigation Report shows an upwards trend in phishing-related cyberattacks.
Phishing is successful and damaging, the results of which can be ransomware, a Business Email Compromise (BEC) scam, data breach, identity theft, and so on. Therefore, it is vital to understand the different types of phishing and the types of cyber-attacks associated. Both organizations and managed service providers (MSPs) can use this know-how to understand better how to prevent phishing attacks.
Did You Know?
cyber attacks begin with phishing
to seamlessly install PhishTitan
estimated global cybercrime cost
to stop & spot a phishing attack
Six Phishing Attack Examples
Email Phishing
This is the most common form of phishing and one that most of us have come across. This type of phishing uses a spray gun approach to phishing. Cybercriminals indiscriminately send out phishing emails to any email address at their disposal. Scammers can quickly obtain thousands of email addresses by harvesting or from email addresses stolen in data breach incidents. Phishing emails contain links to a malicious website or an infected attachment.
What Happens in Email Phishing Campaigns?
Phishing emails are regular occurrences in both private and corporate email inboxes. These phishing emails often impersonate known commercial brands such as PayPal, Apple, and Facebook. These emails will use an individual's trust in that brand to manipulate their behavior. Phishing emails use tactics such as fear of hacking, urgency, or fear of missing out (FOMO) to encourage an email recipient to click on a malicious link or download an infected attachment.
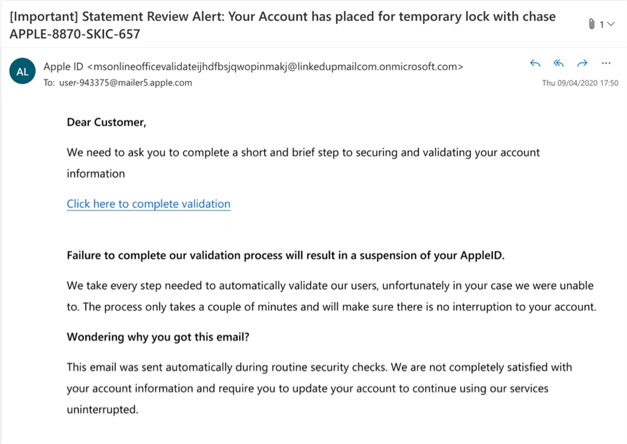
Email phishing can lead to malware infection via an infected attachment in the email. If the recipient clicks on the attachment, the malware will look for vulnerabilities in software on the user's device and exploit these flaws to install the malicious software.
Email phishing can lead to stolen login credentials via an associated spoof website, a user taken to this site if they click on a link in the email or an attachment.
Phishing emails are increasingly challenging to detect as they are designed to evade end user detection. For example, infected attachments such as Word and Excel documents are now less common, and instead, fake image files (.jpeg and .png) are increasingly used to bring malware into people's inboxes.
Spear-phishing
Spear-phishing is a targeted form of email phishing. An Avanti report found some worrying results when investigating changes in phishing volumes. The researchers found that 85% of respondents spoke of "increasing sophistication" in phishing campaigns. Email phishing works, but spear-phishing takes phishing to new levels of success. Phishers take advantage of a lack of IT skills in an organization to exploit a stressed and tired workforce. Suppose a scammer can get the castle's keys (login credentials to corporate networks/apps); they can make a lot of money and cause damage. Spear-phishing targets those in an organization who have access to sensitive corporate resources, such as system administrators, C-level executives, and those working in accounts payable. Phishing emails work in the same way as email phishing, using psychological tactics to manipulate the behavior of their target.
What Happens in a Spear-Phishing Campaign?
A scammer will typically carry out reconnaissance research into a company. This will help them locate a likely target, such as a system administrator, who will have the privilege level to giving the scammer access to sensitive resources. For example, the scammer will compose a realistic-looking email that may spoof a corporate app like a Microsoft Office 365 request to download a vital company document. Suppose the target employee clicks on the malicious link and enters their login credentials or other revealing data into an associated spoof website. In that case, the scammer will use this to carry out the next stage in the attack, e.g., infect the network with ransomware.
Whaling
When spear-phishing scammers go after C-level executives, the phishing attack is known as 'whaling,' aka, catching the big one, a 'whale'. In whaling attacks, scammers will carry out deep reconnaissance of a company, building up the profile of a C-Level executive, such as a CEO or CFO. The resultant spear-phishing email will use extreme tactics and behavioral motivators, such as fear, to manipulate the executive's behavior. For example, the phishing email may contain a threat that the company will be sued to encourage the executive to click on a link or open an infected attachment.
What Happens in a Whaling Attack?
Business Email Compromise (BEC) often has an element of whaling involved. Large and small firms are both at risk of whaling, as this NPR interview with a small business owner discussed: "Mark," an owner of a real-estate firm, told the show how he became a victim of a targeted account takeover attack. Whaling attacks typically try to trick an executive into transferring money or by encouraging a C-level executive to pass approval for the transfer of funds to an accounts payable employee.
Vishing
Vishing is a form of phishing that uses a mobile phone to extract information from an individual or direct them to carry out a behavior that results in stolen data. Often vishing is used in combination with other phishing types, such as spear-phishing. Whaling, for example, may involve an initial phone call from a scammer to extract information that then leads to a whaling email. Vishing covers a spectrum of sophistication, from spray gun-type vishing messages that target the public to focused spear-vishing. The latter may work as part of a scam that steals large sums of money from a business. An excellent example of this was a 2018 scam that involved a phone call that used a fake voice to trick a CEO into transferring $240,000 to a fraudster.
What Happens in A Vishing Attack?
A recent FBI notice explains how scams may use multiple steps during a cyber-attack, some of these steps focusing on privileged users. These attacks often involve reconnaissance using vishing that then utilizes spoof web pages that are used to steal second-factor authentication codes, thereby bypassing traditional forms of protection.
Smishing
What is Smishing
According to Vodafone, around 65% of the world's population regularly sends and receives SMS texts. Businesses and individuals use SMS texts to communicate quickly with others. Organizations from the government, healthcare, banks, and delivery firms use texts to send information and connect with customers. No wonder cybercriminals seize an opportunity in this popular communication channel. Smishing is the SMS text message equivalent of phishing emails. But how do cybercriminals use simple text messages to steal data and infect mobile devices with malware?
TitanHQ delves into SMS phishing or smishing and shows you how to prevent this insidious form of phishing from stealing data and money.
Definition of Smishing
Smishing is a form of phishing. However, instead of using emails to send out phishing campaigns, attackers use SMS text messages. Smishing messages, like their email equivalents, are designed to manipulate the behavior of the target to get them to perform some act that will benefit the cyber-attacker. For example, a smishing message may contain a malicious link to a spoof website. If the recipient clicks the link, they are taken to the website, which will encourage them to enter their personal data and financial details. Sometimes, the spoof website initiates a malware infection of the target's mobile device. Alternatively, some smishing messages request the target to call a phone number to deal with some "urgent need." If the recipient makes the call, they will talk to a scammer attempting to extract personal information and financial details.
Where is Smishing in the Lexicon of Phishing Threats?
Smishing is part of a lexicon of phishing types. Phishing scammers use any communication channel to deliver malicious content that acts to manipulate employees and other individuals. Email phishing is the most well-known form of phishing attacks. However, many forms of email phishing have been developed over the years, including the targeted form, spear phishing. Smishing uses behavioral manipulation tactics like email phishing but is delivered using the mobile phone SMS text message channel.
Read more about the different forms of phishing: “Phishing Attack Examples and How.”
How Smishing Works
Opportunities and Leads: Smishing scammers have many options for carrying out an attack. Ready-made phishing kits and low-cost lists of stolen mobile phone numbers are available for rent or purchase. The dark web has opened opportunities to perform mass-scale smishing attacks. For example, a recent haul of 750 million stolen phone numbers in India was up for sale for $3000 on a dark web marketplace, ideal for a mass smishing campaign.
Tools for Smishing: The tools of the smishing trade are available to buy or rent. For example, Robotech is automation software that sends SMS texts en masse. Organizations like the FTC (Federal Trade Commission) have warned people about scammers using Robotext to send out massive numbers of texts.
The Art of Smishing: GenAI is a new entrant to the smishing scene and will likely be used to generate believable texts to send out using automated delivery systems like Robotext. Getting the text right is essential in any phishing campaign; the content must manipulate deep-seated behaviors, like a feeling of urgency.
Supporting Components: Smishing messages are the initial channel that takes the target to the following interface, usually a spoof website, a mobile app, or even a human on the end of a phone line. The smishing gang can build or rent these components using a Phishing-as-a-Service option on the dark web.
Once all the pieces are in place to carry out the smishing attack, the attackers can proceed. They then wait for the bait to be taken. Recipients of the smishing messages will be lured into handing over financial details and personal data, downloading malware, and so on. Once one campaign is completed, the next will be prepared, then rinse and repeat.
Examples of Phishing Attacks
Like their email phishing counterparts, smishing scammers use many types of smishing attacks to steal data and financial details and initiate malware infections. Some of the common forms of smishing campaigns follow the same patterns as email phishing, that is:
Security Alerts: Phishing messages, whether email or text-based, manipulate behaviors such as fear and uncertainty. Phishers use security alerts to trick targeted individuals into thinking an account has been hacked or a password leaked. The smishing message will tell the target to immediately click a link and enter their login credentials to fix the security issue. The link navigates to a spoof website resembling popular brands like Microsoft 365. If the login credentials are entered, they will be stolen and used to log in to the website.
Free Offers and Gifts: Who can resist a free offer or gift? It is this behavior that smishers rely on to get you to click on a link. Smishing messages that present an unbelievable, too-good-to-be-true offer are likely to be just that - untrue. As with other forms of smishing messages, any link in a gift smishing message will go to a spoof site that steals data.
Delivery Scams: Delivery scams are commonplace in the era of home deliveries. Smishing messages trick recipients into believing a package can’t be delivered. The message typically asks them to click a link to reschedule delivery or pay a fine for underpayment of the postage. The spoof site they are taken to will attempt to steal personal data and money.
App Download Scams: Smishing messages may encourage people to download an app. For example, a variant of the delivery scam instructed people to install an app to track a parcel. However, if the SMS recipient clicked the link to download and install the app, they unknowingly downloaded Flubot spyware that gathers sensitive information, including passwords.
Tax Season Scams: Like email phishing, smishing often follows calendar events, like tax season. Smishing messages usually emulate tax departments, using tricks such as unclaimed tax refunds to encourage recipients to click a link.
Banking Scams: We trust banks to look after our money, and cybercriminals exploit this trust. Smishing messages can mimic a bank's trusted brand, mixing this with concerns and fears. Smishing messages alerting a person to a "hacked bank account" or "unusual activity" in their account may be enough to encourage a link click that leads to stolen bank login credentials.
How to Prevent Smishing from Causing Harm
Smishing can be challenging to detect as attackers use evasive tactics. However, there are specific defensive tactics that an individual and an organization can use to prevent a successful smishing attack:
Learn How to Spot a Smishing Message: Cybersecurity provides a fundamental layer of security. Employees and customers are trained to identify tell-tale signs of smishing, such as being asked to click on a suspicious link. The training will also teach safe internet use and how to identify suspicious websites.
Phishing Simulations: Advanced cyber security awareness training programs like SafeTitan provide phishing simulation platforms that train people to recognize phishing attacks. Phishing simulations are highly effective and can reduce susceptibility to phishing by 92%.
Read a Report on How to Reduce the Risk of Phishing.
Turn on Multi-Factor Authentication (MFA): If a link is clicked and credentials are stolen, having a second layer of authentication reduces the likelihood of a successful attack.
Anti-Phishing Tools: Advanced security tools, like TitanSecure, will block access to dangerous websites, prevent data loss, and stop malware downloads, even if a malicious link is clicked.
Fake Websites
Many phishing campaigns are dependent on fake websites to carry out an attack, so it is essential to note the part that spoof websites play in email phishing attacks. Fake or spoof websites are typically sophisticated and realistic, using similar domain names to the brand they spoof. In addition, the sites usually use digital certificates to make the website look 'secure' - the certificates setting the site URL as beginning with an HTTPS (S for secure). The Anti-Phishing Working Group (APWG) identified 316,747 such websites in December 2021.
What Happens if a User Navigates to a Spoof Website?
The spoof website is often a companion to a phishing campaign. A malicious link in a phishing, spear-phishing, or smishing message, will take a recipient to the companion spoof website. The fake webpage usually reflects the brand that the phishing message spoofs, for example, a Microsoft Office 365 login page. Once the target has navigated to the spoof website, they are requested to enter their login credentials (or other personal details). Once submitted, the data is sent to the hacker behind the scam, who then uses them to log in to the actual site.
Verizon's 2021 Data Breach Investigation Report shows an upwards trend in phishing-related cyberattacks.
Ways to Stop Phishing in all its Forms
Protection against phishing requires a layered approach to anti-phishing protection; by using multiple layers of protection, an organization is more likely to stop the threat before it becomes an incident:
Educate Your Employees
This is a fundamental step in phishing prevention. Security awareness training, augmented with simulated phishing exercises, will make employees aware of the various phishing attack methods.
Choose a Phishing Prevention Platform that is Easily Deployed and Maintained
Effective phishing prevention needs to be scalable across multiple types of devices. The email and content filters must be able to be easily configured and updated from a central console. A cloud-based system provides central management and is suited to deployment and management from a managed service provider (MSP)

Susan Morrow
- DATA PROTECTION
- EMAIL PHISING
- EMAIL SECURITY
Talk to our Team today


