
Cisco Umbrella Roaming Client- End-of-Life
Geraldine HuntThe imminent Cisco Umbrella Roaming Client End-of-Life has left many users uncertain about their next steps and exploring alternative DNS protection.
Brexit news has been dominating headlines lately, and attackers have taken advantage of the public’s constant attention on the latest developments. From Trojans to phishing scams, attackers have sent emails tricking users into opening links that contain malware in an effort to steal sensitive data such as login credentials or financial data.
Although hackers use various methods and designs for phishing emails, the concept behind the attacks was usually the same – an email with Brexit design and text tells users to click a link that then brings a targeted user to an attacker-controlled web page. The email looks official, and attackers put together a well-designed layout.
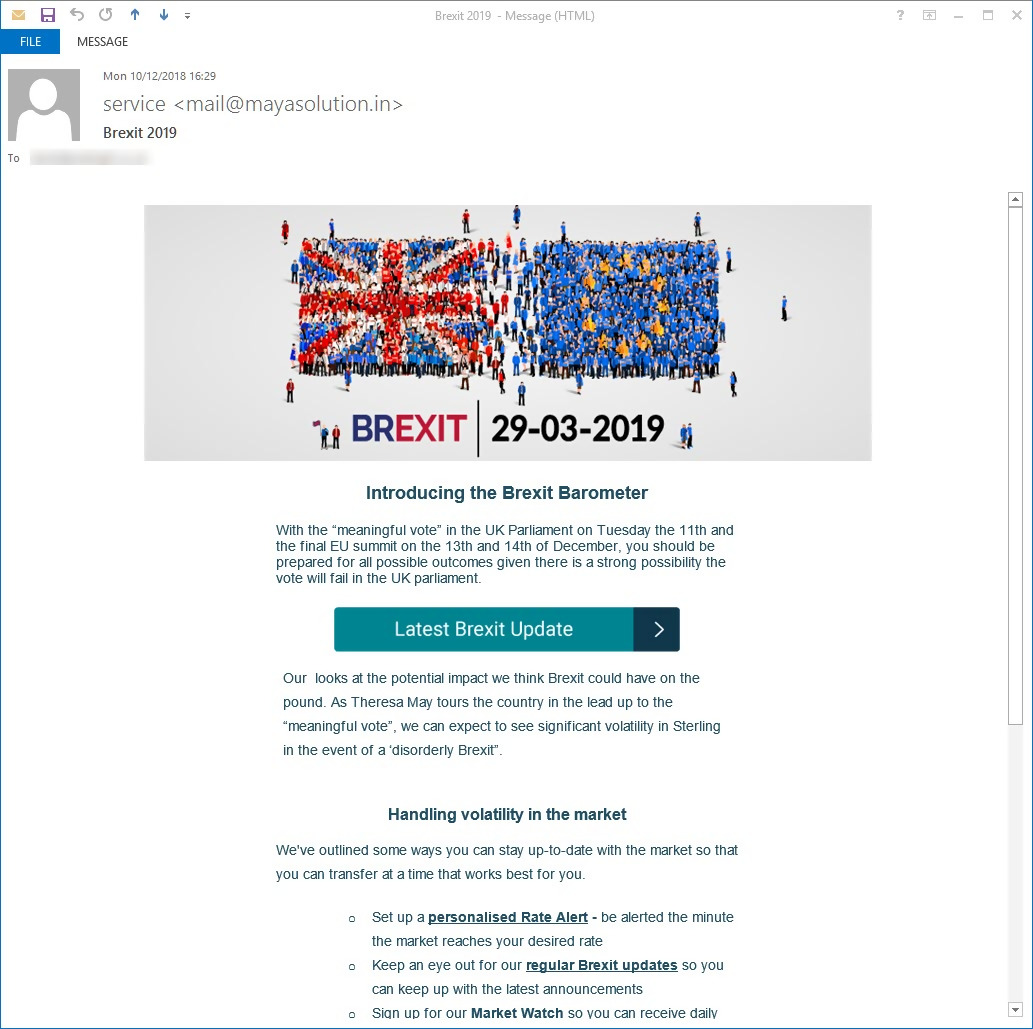
(Example email)
When the user clicks the link in the email, either a document downloads or users are brought to a web page where they are prompted to download malicious applications. Attackers even went so far as to give the document the same name as the official one published by the European Union. These types of small, easy techniques can have a big impact on the attacker’s ability to trick users into opening the file.
The file users download contains macros, which are then used to download malicious Trojan software. Trojan software can download additional malware, give attackers remote access to a user’s local machine, or record and send sensitive data. The Brexit document installs malware that records data entered by users. This data could be passwords to an online site, financial data or additional information that gives attackers access to the user’s online accounts. By default, macros are disabled in applications such as Microsoft Word, so users must allow the macro to run before it can affect the local device. The document contains messages convincing the user to allow the macro to run by claiming content cannot be seen unless the user runs the malicious script.
Phishing emails surround Brexit news asked users to enter personal information, log into a web page with banking credentials to monitor currency fluctuations and posed as government agencies asking for sensitive data. Because the Brexit event has been a political nightmare for residents, the scam was able to trick users into divulging much of their data that was later used for future financial attacks.
Events such as Brexit or any major political incident are known to trigger outrage from users, and it’s these emotional triggers that attackers use to bypass most user suspicions when they receive an email from an unknown recipient. Users should still be vigilant about their data and privacy even when a message looks like it’s from an official representative of any organization.
Users and corporations can take several steps to ensure that they do not fall victim to any of these scams. For individuals, some free email services such as Google have good filters that block spoofed email messages. Messages are sent directly to the user’s spam inbox so that they are never seen. Messages identified as suspicious have a red warning label.
Corporations must make larger strides to educate and protect users because the data available on an enterprise network is much more valuable. Attackers with user credentials to the local network or remote control of an enterprise network device can gather gigabytes of data and siphon it to an attacker-controlled server. For this reason, the local enterprise network needs more than just user training, although cybersecurity training has been known to reduce successful phishing attacks.
Email filters are the primary defense for corporations. These systems quarantine suspicious messages based on a set of cybersecurity rules set up by the email administrator. Administrators can review the quarantined messages and either send them to the user’s inbox or delete them from the system. These email filters reduce the chance of users ever receiving spoofed email messages that contain malware or ask users to enter sensitive information.
An additional option is to add DNS-based web content filtering. Should a false negative get routed to a targeted user’s inbox, DNS-based web content filtering will stop the user from being able to access the malicious website. This block on malicious sites would not stop the user from sending information in an email, but it would help reduce data leaks from users entering information on attacker-controlled sites.
Even with data privacy measures in place, corporations should continue giving cybersecurity training to users. Training users to detect phishing scams such as the Brexit attack will greatly reduce successful attacks including sophisticated ones using social engineering. Always have email filters set to quarantine suspicious messages, and block known attack sites from user devices.
Any email that contains a link to a news story should be deleted. The story will be covered by the usual news websites if it is genuine. Those sites should be accessed directly through the browser or via the search engines.
Organizations can protect their networks and users from Brexit phishing attacks and other malicious spam email campaigns by installing a spam filtering solution such as SpamTitan. SpamTitan captures more than 99% of spam email, preventing phishing emails from being delivered. This reduces reliance on employees being able to identify a phishing scam or malicious email.

The imminent Cisco Umbrella Roaming Client End-of-Life has left many users uncertain about their next steps and exploring alternative DNS protection.

School districts around the world over are issuing Chromebooks to students to help close equity, technology and homework gaps. Discover why and how to protect K12 students.

A 2024 report highlights the soaring popularity of QR codes, with a 47% yearly usage surge. However, cybercriminals are exploiting this trend, targeting unsuspecting users with scams and malware infections due to...
Sign-up for email updates...
