
Cisco Umbrella Roaming Client- End-of-Life
Geraldine HuntThe imminent Cisco Umbrella Roaming Client End-of-Life has left many users uncertain about their next steps and exploring alternative DNS protection.
It’s not uncommon for email recipients to look at the sender of a message and never check if the sender is the official address. Spear phishing usually involves an attacker tricking an employee into sending money to an attacker-controlled bank account or tricking an employee into disclosing credentials, but phishing can also be targeted towards a brand’s customers. Using a brand, an attacker can phish credentials from targeted users to steal their data or access financial accounts.
Although many brands are used for this type of attack, PayPal was one of the most popular brands used to steal user data. Attackers would send phishing emails using the PayPal log and a spoofed or similar domain name in the sender’s address.
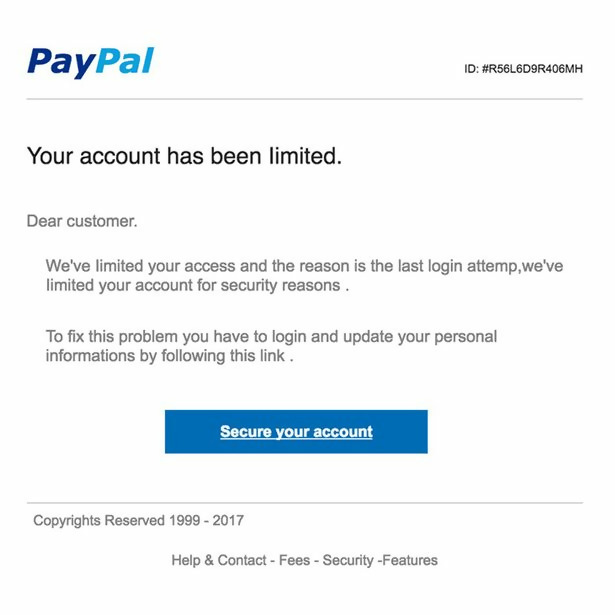
The above image displays a sample PayPal phishing email using the PayPal brand. Notice the logo, copyright message and a button that links to a page. Aside from the typos and poor grammar, one red flag is that the email does not address the user. When PayPal sends email, they address the customer by name. Although this is a good red flag, even if this email had the first name of the targeted user, the recipient should still be suspicious.
The button will take the user to an attacker-controlled server where the attacker might try to install malware in the browser, but the most common landing page is on an attacker-controlled server with a page that looks like the official PayPal page. The landing page might be on a domain that looks similar to PayPal or it might have the PayPal brand in a subdomain name. On occasion, the landing page is in a subdirectory on the attacker’s domain. Since the goal is to trick targeted users, the naming scheme for the landing page will be similar to PayPal’s.
From the image, you can see that the email is very convincing. A targeted user unfamiliar with phishing or not very tech savvy would click the link. With a convincing website, the user might very well send credentials to an attacker. PayPal has several security defenses in place to protect users that have been phished, but attackers are still able to get through these defenses occasionally.
The above example uses PayPal to illustrate the issue, but a big popular brand isn’t the only target for attackers. They use smaller brands, banks, and even friends’ names taken from a user’s social media account. In other cases, the attacker could get access to a targeted user’s email and use their own contact list to send a phishing email. Because the brand or recognizable user is trusted by the recipient, the recipient is more likely to fall for the phishing attack.
These attacks plague small and large businesses. While the previous example was geared more towards a personal PayPal account, attackers also use banking sites to phish employee and contractor credentials. The infamous Target data breach where attackers were able to exfiltrate 40 million credit card numbers from consumers. The result was an investigation, lawsuits and millions in restitution.
No cybersecurity defense is 100% secure, but the best way to protect users is by using email filters. DNS-based content filters along with an email system that incorporates DMARC (Domain-based Message Authentication, Reporting & Conformance). DMARC is the de facto cybersecurity system to protect users from phishing and spoofed email addresses.
DMARC is a set of cybersecurity rules created by the email administrator. It incorporates two technologies: DKIM (DomainKeys Identified Mail) and SPF (Sender Policy Framework). These two technologies work together to verify that the sender is really the official address and not an attacker using a spoofed address. DKIM uses public-private key encryption to create a signature in the headers of an email, and SPF utilizes DNS-based verification entries set by the brand’s IT administrator. These two technologies create DMARC verification rules.
The system administrator can create levels of DMARC rules to determine if suspicious flagged messages are dropped and deleted or quarantined. Quarantined messages can be reviewed by an administrator and released to the recipient’s inbox should it be harmless. DMARC systems also have reporting functionality so that an administrator can identify any false positives and adjust settings as needed.
Without phishing defenses, a business is highly vulnerable to phishing and malicious content. DMARC email systems along with other effective cybersecurity protect a business brand and stop attackers from using well-known companies to trick users into disclosing their credentials.

The imminent Cisco Umbrella Roaming Client End-of-Life has left many users uncertain about their next steps and exploring alternative DNS protection.

School districts around the world over are issuing Chromebooks to students to help close equity, technology and homework gaps. Discover why and how to protect K12 students.

A 2024 report highlights the soaring popularity of QR codes, with a 47% yearly usage surge. However, cybercriminals are exploiting this trend, targeting unsuspecting users with scams and malware infections due to...
Sign-up for email updates...
