Home /
TitanHQ Blog /
Email Impersonation (Spoofing) on the Rise: 74% of Data Breaches Caused by Human Element
Posted by Selina Coen on Tue, Aug 22nd, 2023
Business Email Compromise (BEC) is on the rise and is one of the costliest threats today. In 2022, 60% of email compromises were from social engineering, with 74% of data breaches caused by the human element. Ransomware, malware injection, credential theft, and money theft are just a few consequences of a successful BEC attack. Every year, BEC costs businesses billions, and it’s expected to rise tremendously by 2027. It’s more important than ever that businesses find effective ways to stop email-based threats.
The State of BEC in 2023
Every year, Verizon publishes its Data Breach Investigation Report (DBIR). This report covers the state of the cybersecurity landscape worldwide and specific threats commonly launched against businesses. In 2023, BEC was one of the most common pretexts for a data breach. Business email compromises were the start of malware injection, ransomware, or other nefarious strategies used in advanced persistent threats.
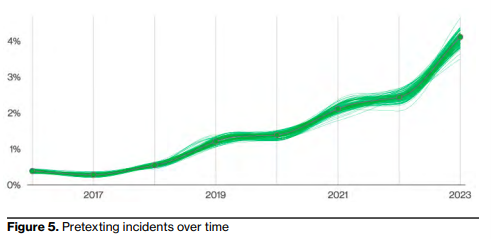
(Verizon DBIR 2023)
Email-based threats in more significant data breaches have doubled in the last two years, making them one of the costliest for businesses without any cybersecurity infrastructure to stop them. Many organizations rely on human intervention to prevent phishing and social engineering, but it’s insufficient. The human element remains the weakest link in every enterprise environment, and the data proves it. Verizon’s DBIR indicates that 74% of data breaches involve a human element, mainly via a phishing email or type of social engineering combined with an email threat.
Second to email-based threats is ransomware. Ransomware often goes hand-in-hand with email threats. The attack starts with an email, probably targeted towards several employees with elevated privileges on the corporate network. Only one employee must fall for the email threat, and it gives ransomware access to the internal environment.
After the ransomware obtains access, it can now deliver the malicious payload. A ransomware payload depends on the author’s programming, but ransomware usually encrypts and steals data, leaving the organization unable to stay productive. Organizations must recover from backups or pay the ransom, but ransomware has residual effects from lost productivity and data, downtime, compliance violation costs, and litigation from affected customers.
Third-Party Email Service Providers are the Biggest Targets
It’s not uncommon for organizations to rely on third-party email services such as Microsoft Outlook 365 or Google Suite (Gmail) to manage the security of inboxes. While these services offer cybersecurity and filters, they don’t completely block suspicious email messages. Take Google’s Gmail service as an example. Google automatically categorizes suspicious email messages and puts them in the user’s spam inbox. While this removes the message directly from the user’s inbox, users habitually review the spam inbox for any missed messages. They then fall victim to various scams and phishing threats.
Because cyber-criminals know that organizations rely on third-party email services, they are often bigger targets than the corporations themselves. As recently as June 2023, Microsoft was the target of a sophisticated attack on its Outlook 365 and OneDrive platforms. Microsoft Teams is also a proxy for business email compromise. With a hacked Teams account, attackers can access the user’s inbox.
Google Workspace is also a target, especially for enterprise users. Cyber-criminals craft malicious links asking for OAuth access to user Gmail accounts. If an employee does not notice that the requestor and URL are from an unknown URL, the employee could mistakenly provide access to a malicious third party. With access to a user’s inbox, cyber-criminals can access sensitive data and impersonate the hacked employee.
In a business email compromise, it’s common for cyber-criminals to target executives and other prominent employees. With an executive email, the hacker can now send emails pretending to be an executive and ask for money transfers, sensitive business intellectual property, or convince other employees to download malware, particularly ransomware. Because the message comes from a legitimate user, business email compromises are much more effective than a general phishing strategy.
What Can Businesses Do to Stop Email Spoofing?
Cybersecurity is integrated into third-party service providers, but businesses need additional protection to stop sophisticated email threats. Good cybersecurity strategies always involve overlapping layers of protection where one layer takes over should another fail. Email filtering solutions under the primary third-party filters take over as a failsafe should the provider suffer from a targeted attack on employee inboxes.
Email filtering solutions such as SpamTitan use artificial intelligence to analyze incoming messages and file attachments and rate them for suspicious content. If any content is considered malicious, the email filtering software will transfer it to a quarantine location in the corporate environment. The quarantine location is only available to administrators, so users cannot scan through quarantined messages and interact with what could be a legitimate threat.
Administrators can review quarantined messages and pass them to the intended recipient or review them further for any telltale signs of a targeted threat. Targeted threats should be communicated to employees, so they know and take precautions. Security awareness training is also necessary, but many organizations are targets of zero-day threats to bypass typical employee cybersecurity education. Even people with extensive cybersecurity training can fall victim to phishing and social engineering, so email filters should be the first layer of protection before messages reach an intended recipient.
By removing any interaction from employees, businesses’ security awareness training exercises are the third layer and a failsafe for email filters. Businesses have the third-party service provider’s filters, their email filtering solution, and another failsafe from security awareness training. All three security protocols reduce the risk of a business email compromise to a tiny fraction.
Security awareness training such as SafeTitan is necessary for a cybersecurity strategy, but training is something that only some corporations can offer. It’s the one aspect of cybersecurity most corporations are missing, but they don’t have the experience to deploy the necessary training.
To take a look at what SafeTitan security awareness training can do for your business, book a free demo.
Fortify your defences against rising email impersonation and BEC threats with SafeTitan!
Book Free Demo



