
Cisco Umbrella Roaming Client- End-of-Life
Geraldine HuntThe imminent Cisco Umbrella Roaming Client End-of-Life has left many users uncertain about their next steps and exploring alternative DNS protection.
Phishing emails are always a concern for organizations, but Emotet is phishing, malware, ransomware, identity theft, and spamming malware in one attack. Although Emotet has been active since 2014, it’s become increasingly more popular in the last few months. If your organization deals with email and receives documents as attachments, it’s imperative that your email cybersecurity has controls in place that detect and block Emotet.
What is Emotet?
Discovered in 2014, Emotet was originally malware that stole user banking credentials. It started as trojan malware that ran on a user’s computer and stole sensitive information as the victim browsed the internet and entered banking data. It started with a phishing email that encouraged users to open the document. The malicious Word document contained a macro that would download and run the trojan.
What started as phishing and credential theft malware, Emotet has evolved to be much more virulent and even has a worm element to it that helps it self-replicate more across the Internet. Now, Emotet has a ransomware element that scans a victim’s network, finds sensitive data, and encrypts files with the attacker’s private key. If the victim does not pay the ransom, the attacker does not deliver the private key and files stay encrypted. The only way to recover from ransomware of this magnitude is to restore files from a backup.
Emotet has gone through several iterations to avoid discovery from anti-malware programs. It sometimes arrives in email as a JavaScript attachment instead of a Word or Excel document. Some versions of Emotet using Word documents will give an attacker remote control of the local device and download malware from a central attacker-controlled server.
To avoid detection, Emotet will lay dormant if it determines that it’s running in a virtual machine. Virtual machines are often used to observe malware so that researchers can determine its payload and create anti-malware procedures. Emotet lays dormant to avoid researcher observation to make it difficult for them to create ways to stop it from delivering its payload.
Emotet in 2020
Emotet has had several iterations, but it’s made a comeback in 2020 as a major threat against organizations. Creators of the malware and the cyber-criminals that use it have new phishing emails tricking users with holiday-themed messages. The payload installs TrickBotand Qbot on user devices to steal banking credentials, but some variants allow an attacker to use the device in distributed denial-of-service (DDoS) attacks and take control of the device as a part of the attacker’s botnet.
New messages seen in the wild include a Halloween email that tell the recipient that they’ve been invited to a party. The message encourages the reader to open the Word attachment, which includes a malicious macro. Word has macro execution disabled by default, but users see an “Enable Content” button used to run the macro.
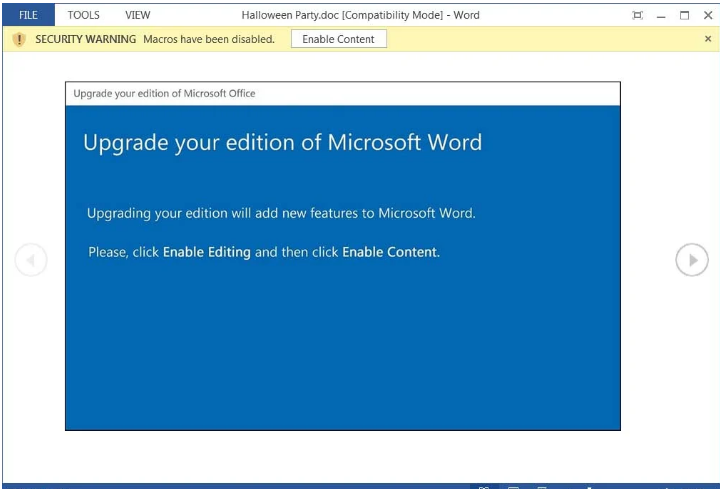
If the user clicks the button, the macro runs and downloads malware. The trojan malware could include credential-stealing software and ransomware. If ransomware is included in the payload, it will scan the user’s network for files and encrypt them. Ransomware cannot scan cloud drives, so cloud backups can be used to recover and restore encrypted files.
Emotet has a worm feature with it, which means that it will scan the user’s contact list and send emails to your friends and family encouraging them to open the Word attachment. Because of the worm feature, Emotet spreads quickly and continues to be a large threat in cyberspace. If users receive a holiday party email with an attachment, the message should be deleted without opening the file.
Protecting Organizations from Emotet
The ransomware aspect of Emotet is especially concerning for organizations. Ransomware comes with scanning abilities that will find vulnerable files and encrypt them. For organizations, this can be devastating for productivity and can halt work-related functions. For organizations with no backups or ways to stop ransomware, a successful attack can leave them unable to function. It’s not uncommon for some organizations to pay the ransom, but there is no guarantee that the private key will be provided for file recovery.
To combat email-based attacks, organizations should implement email security. Email security can be applied to an on-premise server or one hosted in the cloud. The recipient email server can be configured to completely reject messages with attachments, but this option is not acceptable in many organizations that must allow outsiders to send documents to employees. The other option is to use a cybersecurity application that will detect malicious attachments and messages and quarantine them. This option lets administrators send messages to the intended recipient after it has been reviewed and verified.
Emotet scans a victim’s contact list and sends email using the device owner’s account, so spoofing is not necessarily a part of this attack. Spoofed messages can be blocked using a Sender Policy Framework (SPF) entry on DNS servers, but this only stops messages where an attacker uses an open email server to send messages that look like they come from an official source.
For malicious attachments, the organization needs a cybersecurity solution that can identify documents with malicious macros. The email is quarantined for administrators to review, because artificial intelligence (AI) cybersecurity solutions occasionally incorrectly detect malicious macros. The administrator reviews and either permanently deletes the message or sends it to the recipient’s inbox.
Another benefit of quarantining messages is that several incoming malicious emails could mean that the organization is a target for a strategic attack. Several messages sent to key employees could mean that the organization is a target for spear-phishing. An administrator can then notify employees that an increase in phishing emails are currently targeting employees with higher level privileges. Using email cybersecurity and user training, organizations can be much more secure against Emotet and other email-based attacks.
User training helps defend against phishing attacks, but Emotet is a sophisticated campaign that requires better cybersecurity than standard training. The ransomware and credential theft could be result in devastating data loss and compromise for a large enterprise. By using email cybersecurity such as TitanHQ, your organization can defend against the latest phishing attacks with malicious attachments.

The imminent Cisco Umbrella Roaming Client End-of-Life has left many users uncertain about their next steps and exploring alternative DNS protection.

School districts around the world over are issuing Chromebooks to students to help close equity, technology and homework gaps. Discover why and how to protect K12 students.

A 2024 report highlights the soaring popularity of QR codes, with a 47% yearly usage surge. However, cybercriminals are exploiting this trend, targeting unsuspecting users with scams and malware infections due to...
Sign-up for email updates...
