
Cisco Umbrella Roaming Client- End-of-Life
Geraldine HuntThe imminent Cisco Umbrella Roaming Client End-of-Life has left many users uncertain about their next steps and exploring alternative DNS protection.
Although Palmerworm mainly stayed hidden since 2013, a recent Symantec report found that the malware has had more persistent activity in 2020 and even remained on an undisclosed corporate network for almost six months. Attackers behind Palmerworm have added new malware to the advanced persistent threat (APT) aimed at mainly media and financial groups in the US, Japan, Taiwan, US, and China.
How Palmerworm Tricks Users
Although Symantec was unable to determine the initial attack vector, but it’s assumed that it starts with a phishing campaign. Palmerworm uses a unique approach to tricking users into running malicious content. Included in the malware is stolen signed certificates making users believe that the software is legitimate.
Code-signing is a way to tell operating systems and users who created the software. When users attempt to install software, the operating system displays the publisher. The publisher uses a signing method using specific keys only available to the publisher. An example of a code-signing message is below: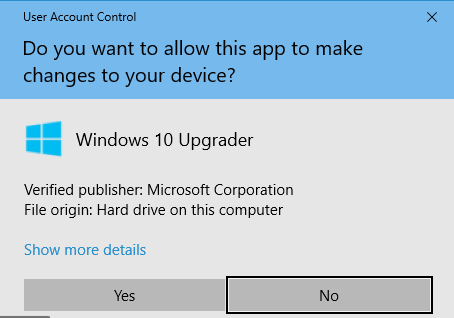
In the above image, the user can see that the publisher is Microsoft and will allow the program to proceed. Palmerworm authors use stolen code-signing keys to sign software, which makes it highly likely that users will run the malware.
Palmerworm uses custom malware and some freely available software to deliver the payload. The malware is a group of backdoors giving the attackers access to the network and allows them to persist on a corporate network even after administrators think that it’s been removed.
The custom malware included with Palmerworm are:
The software included that helps Palmerworm install and scan the network includes:
The backdoor malware gives attackers a high level of access across devices. Once an attacker has full control of one device, the malware can be spread across other devices on the network. The network reconnaissance and administration tools help the attacker find additional vulnerable devices so that backdoors and remote control can be established
Palmerworm Targets
This latest Palmerworm campaign is targeted towards organizations in several countries including US, Japan, Taiwan, US, and China. According to the report, the biggest target is media organizations in Taiwan and construction companies in China. The third largest target is finance companies in Taiwan.
Palmerworm also targets several corporations in the report does not specify the company name, but Palmerworm maintained a presence on a US corporation for almost 6 months and other US-based devices. The advanced way Palmerworm infects networks make it difficult for administrators to detect it if the right tools are not in place.
Because Palmerworm targets businesses, the initial report believes that the attacker’s goal is to steal intellectual property and sensitive data contained within the business environment. More information and observation are needed to find out more about Palmerworm, businesses must take necessary precautions to ensure that the malware is not able to inject itself onto corporate devices.
Taiwan reported that they believe the Chinese government is behind the attacks, which included 10 government agencies and 6000 government official accounts. From Taiwanese observation, the attacker’s goal was to steal important government documents and sensitive data.
You might be interested to read a recent article discussing the 'Top Malware Trends to Watch For in 2020
Protecting Your Organization from Palmerworm
Palmerworm is not a new advanced persistent threat. It’s been around since 2013, so good anti-malware programs can detect and stop the backdoors from installing on a device. Organizations with enterprise-level anti-malware should have it installed on all devices including desktops and mobile smartphones.
Because it’s believed that Palmerworm starts with a phishing campaign, it’s even more important than ever to implement email filters. Content filters will also stop users from accessing malicious sites where attackers could host Palmerworm malware and trick users into downloading it. Email filters will block malicious emails with attachments that could contain Palmerworm malware or macros that will download it form an attacker-controlled server.
Educating users on the dangers of phishing and identifying red flags associated with phishing also helps. Users with proper education are less likely to download malicious content or open attachments. They will also be aware of suspicious links from untrusted senders.
TitanHQ provides a cloud-based solution for email filters that blocks Palmerworm and other advanced persistent threats. Using our cloud-based WebTitan platform, your organization will be protected from Palmerworm and other web-based attacks that require users to first access an attacker-controlled site where malware can be downloaded and installed.
Malware creators continue to create new ways to evade detection, and Palmerworm-like malware could lead to large breaches in 2020 and beyond. By focusing on reducing the attack surface, this threat can be mitigated with robust security controls. Organizations can get ahead of these attacks by implementing DNS-based filters like WebTitan which detects malicious files, scripts, as well as blocking access to malicious URLs.

The imminent Cisco Umbrella Roaming Client End-of-Life has left many users uncertain about their next steps and exploring alternative DNS protection.

School districts around the world over are issuing Chromebooks to students to help close equity, technology and homework gaps. Discover why and how to protect K12 students.

A 2024 report highlights the soaring popularity of QR codes, with a 47% yearly usage surge. However, cybercriminals are exploiting this trend, targeting unsuspecting users with scams and malware infections due to...
Sign-up for email updates...
