
Cisco Umbrella Roaming Client- End-of-Life
Geraldine HuntThe imminent Cisco Umbrella Roaming Client End-of-Life has left many users uncertain about their next steps and exploring alternative DNS protection.
Data breaches are a widespread problem. From leaked business information to disclosed customer addresses, a data breach can quickly transform into a crisis. Compromised data exposes a company to new vulnerabilities. The Covid -19 pandemic is thought to be at the heart of a rise in security incidents this year, with many employees still working remotely.
More and more criminals are gaining access to large amounts of stolen personal data at ever-cheaper prices. Gaining access to this data is not difficult which is why there’s so much stolen data available. The average going price for stolen credentials tied to popular e-commerce and banking sites is a mere $15. Even a credit card number with its corresponding CVV only goes for $12, oftentimes even less. The price goes up to $25 for credit card data that is paired with the cardholder’s date of birth and bank identity number. While your individual credentials may not be worth all that much, the possible damage that can result to you financially can be hefty.
A study conducted by Google and the University of California Berkeley found that billions of usernames and passwords are at risk. The involved research team tracked several black markets that sold stolen credentials. These credentials were compromised through data breaches as well as some 25,000 hacking tools. Deeper analysis showed that 788,000 credentials were stolen via keyloggers, 12 million credentials through phishing and 3.3 billion through third-party data breaches. Keep in mind this data is more than 2 years old.
In February 2019, more than 617 million online account details stolen from 16 hacked websites were being sold for less than $20,000 in Bitcoin according to an article in Forbes Magazine. Says one cybersecurity analyst, stolen usernames and passwords are “traded like Pokémon cards.”
For those who access the dark web, shopping for stolen credentials has truly become a retail-like experience. According to Brian Krebs from KrebsonSecurity.com, credentials are being sold in retail like fashion. These retail sites list the involved website, the sale price and current inventory on hand. Actual examples of what you can find from one of these sites include the following: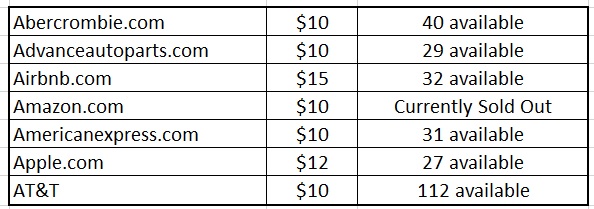
By the way, we only included the biggest names from the A’s. Many of these sites sell more than just credentials. For instance, you can purchase someone’s identity. The identities of these unknowing victims are even indexed according to FICO score. An identity with a near-perfect score above 840 can go for $150. Full credit reports are also for sale on millions of Americans from all three credit bureaus. These go for as little as $35. You can even purchase diplomas for $100-$400. Passports are the real prize, garnering as much as $2,000.
A number of factors determine prices for stolen credentials. These include:
The introduction of “automated shops” provided a convenient marketplace for stolen credentials. Think of them as an eBay or Amazon retailer in which the smallest of independents can sell their goods to the world through a single global retailer. These automated shops give cybercriminals a means to sell the credentials they steal. Stealing credentials today does not require extensive cyber or programming experience. Low-level cybercriminals can purchase credential-stealing kits for $550 on the dark web, a nominal fee that can produce a return of 20 times the initial investment. The automated shops charge a 10 to 15 percent commission for each sale and provide customer and vendor support. They will even help resolve transaction disputes. Welcome to the digital transformation of cybercrime.
In the same that there are established processes that retail products go through from the time they are manufactured to the point at which a consumer might purchase it from a first level retailer, or a discount store months later, stolen credentials go through a defined process as well in order to reach these automated stores. The first step in the chain is an inventory of the data.
Hackers that manage large-scale bot networks or implement data breaches will sort through their log files to determine what type of data they have recently captured. They then correlate this data in order to package personal information in order to complete data profiles. Stolen credentials that can be appended with names, addresses, phone numbers, email addresses, etc. are more valuable.
High-value data such as the personal data of government workers or military personnel are set aside. These personal data packages are then sold as profiles while unmatched credentials are sold. Eventually, the compromising of these accounts is discovered, making most of them worthless. Stolen credentials that have some age on them are repackaged into bulk lists and can be sold at cut-rate prices for years.
According to IBM’s Cost of a Data Breach Report 2020, when the majority of employees work from home, 70% of respondents believed that a remote workforce would increase the cost of a data breach. There are many reasons this might be the case. Without employees on the premises, it may be harder to identify issues as quickly. Security incidents may also impact remote workers access to email or company data or other essential communication tools. This kind of disruption, specifically email and data continuity, can severely affect productivity or force employees to stop working altogether.
Password Hygiene
A password can be the last line of defense for a remote device or SaaS application. Password policies that enforce minimum complexity standards are essential outside of the confines of the secure perimeter.
Multifactor Authentication
When an employee is onsite, their passwords are supplemented by local security measures but this is not the case when offsite. Outside of a web conference, it is impossible to confirm who the faceless identity is at the other end of a connected session. As a result, passwords alone cannot be relied upon when employees are offsite. The authentication process for essential services such as email and sensitive cloud services should be backed up by multifactor authentication such as the confirmation of a text sent to the employee’s cellphone.
Computer Use Policy
It is important to have a computer use policy for remote employees stating that the computer devices used for work are designated as work devices only and that it should only be used by the employee.
Web Content Filtering
Most web content filtering solutions today integrate with Active Directory or LDAP, allowing management to monitor the internet activity of all employees. When a remote computer establishes a VPN connection, the web session runs in the same fashion as if the device were located on premise.
Thanks to cloud-based DNS filtering solutions, all work-related devices can have the benefit of umbrella-like web filtering protection. Whether working permanently from home or on the go utilizing public WiFi, a cloud-based content filtering solution such as WebTitan can combat malware, spam, malvertising, malicious files, ransomware and annoying popups. No matter where the device is, your users remain protected.
Endpoint Protection
While the combination of email and web filtering can stop the majority of threats today, a multi-layered security approach is essential in today’s digitally dangerous world. Every work device needs to be protected by an endpoint security solution. Often times these solutions serve as a last line of defense. Ensure that all devices, both mobile and desktop, are protected with adequate security before your employees can use them to log in to your network.
Training employees on security best practices will go a long way. It's important to teach employees how to spot potential phishing scams and explain the importance of strong passwords. While a device may be remote in terms of distance, malicious files that infect your remote devices are only a click away from invading the enterprise. Just because a device is off-site, it should never be out of mind.
Would you like to learn more about keeping your remote workers data secure?
Talk to a specialist or Email us at info@titanhq.com with any questions.

The imminent Cisco Umbrella Roaming Client End-of-Life has left many users uncertain about their next steps and exploring alternative DNS protection.

School districts around the world over are issuing Chromebooks to students to help close equity, technology and homework gaps. Discover why and how to protect K12 students.

A 2024 report highlights the soaring popularity of QR codes, with a 47% yearly usage surge. However, cybercriminals are exploiting this trend, targeting unsuspecting users with scams and malware infections due to...
Sign-up for email updates...
