Business Email Compromise (BEC) scams focus on stealing money from businesses like yours. They utilize a mix of phishing, social engineering, and sometimes malware infection to manipulate staff, including C-level executives. The result is transferring your company's money into a cybercriminal's bank account.
In 2023, BEC attacks cost businesses an estimated $2.9 billion; the FBI IC3 received 22,189 BEC complaints during 2023. BEC is the second costliest of cybercrimes, with an average cost of $124,000, an increase from $120,000 in 2021.
BEC is a global crime that increasingly targets small- to medium-sized organizations (SMBs). In Q3 2023, 64% of identity-related cyberattacks on SMBs involved malicious email and phishing activity associated with BEC.
Did You Know?
cyber attacks begin with phishing
to seamlessly install PhishTitan
estimated global cybercrime cost
to stop & spot a phishing attack
Methods and Tactics in Business Email Compromise Attacks
BEC scams are out of control, soaring by 81% in 2022, with almost 98% of affected employees not reporting the attack. Sophisticated phishing scams, such as QR code phishing, are improving the chances of Business Email Compromise. With this threat level and the success rates experienced by BEC scammers, businesses should be on their guard.
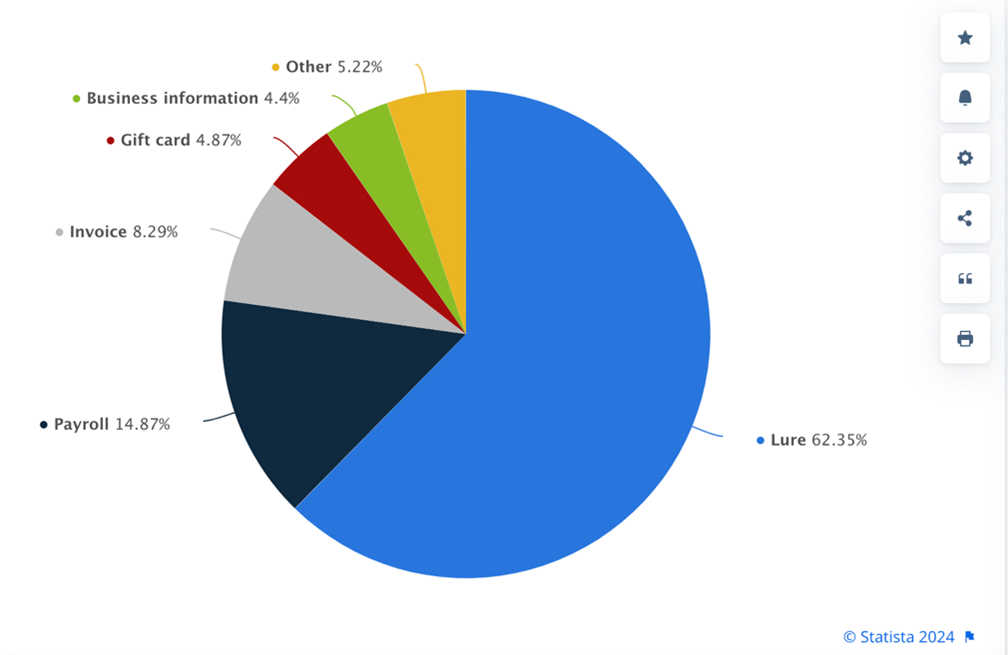
The following methods are typical of BEC crimes:
Phishing (of all kinds)
Phishing is a fundamental mainstay of BEC scams. Phishing, including spear phishing, QR Code phishing, and other forms of phishing, are used to initiate the BEC attack chain. For example, BEC is simplified if an executive's email account is compromised. Targeted phishing emails are used to steal login credentials to access email accounts. Alternatively, phishing emails may be used to install malware that goes on to steal login credentials.
Phishing is increasingly used in multipart, social engineering-based attacks. For example, emails lure employees into sharing confidential details of suppliers by socially engineering the recipients. These details are then used to send fake invoices to the company and suppliers.
Invoice Scams
Examples of invoice scams are everywhere, but a 2023 example shows how damaging BEC crimes can be. A coach operator lost a five-figure sum due to a fraudulent invoice. The scammers compromised employee email accounts and then watched for incoming invoices. Once a suitable invoice was identified, it was intercepted and adjusted, changing the payee bank sort code and account number to the hacker's own. In this case, the scammers went a step further, asking for the funds to be split between several accounts; this would prevent alarm bells ringing during the transfer.
In a modern twist on invoice fraud, GenAI is being used to create fake invoices and empower BEC scams.
Attorney Impersonation
There has been a recent spike in BEC attacks based on the impersonation of an attorney (solicitor). The Law Society of Scotland has collected some scam details, including the following BEC fraud that works similarly to fake invoice scams: A fraudster compromises an attorney email account, typically phishing. Once an email account is in the hands of the attacker, they can then watch for specific lucrative transactions, like house sales. Once identified, the hacker intercepts the relevant email and changes the payment details.
Microsoft 365 and CEO Fraud
Popular productivity apps, like Microsoft 365, are targeted by fraudsters who mimic the brand. Microsoft 365 and BEC scams go together, with CEO fraud often used with M365 BEC scams. Vendor Mitiga, identified a BEC scam that targeted C-Level executives using M365. This BEC attack used a flaw in M365 to circumvent MFA authentication. The attackers used complex, multi-part phishing and social engineering tactics to take control of the executive email account. Once compromised, the C-level exec account was used to send out a change of payment details when a significant transaction was identified.
As you can see, BEC attacks may have a different focus, but they all use similar tactics, namely phishing and social engineering. Other techniques may involve software vulnerabilities and malware, but whatever technique is used, Business Email Compromise remains a considerable and complicated threat. However, there are ways and means to mitigate this threat.
In 2023, BEC attacks cost businesses an estimated $2.9 billion; the FBI IC3 received 22,189 BEC complaints during 2023.
Best Practices to Prevent Business Email Compromise
One of the difficulties in dealing with a BEC attack is its multipart nature. Add sophisticated social engineering into the mix, making it increasingly challenging to detect and prevent Business Email Compromise. However, there are best practice measures that significantly reduce the chances of a successful BEC scam stealing your company’s funds. The main takeaway is to use multiple layers of protection that include the following:
Include BEC Scams in your Security Policies
Ensure that the complex nature of BEC attacks is included in security policies. This will establish a company-wide initiative to ensure that BEC is taken seriously and that measures are taken to prevent those attacks.
Leverage Multiple-Factor Authentication
MFA may be circumvented in some circumstances, but it is still an important layer of security. Having MFA in place is like having a moat around a castle. If the cybercriminal has a boat, they can get across, which makes it more difficult.
Verify Transactions
Large payments and purchase requests should be verified. This could be done by phone calls rather than emails. However, deep fake voices complicate this measure; verified transactions should be considered an additional layer rather than a single-point fix.
Train Employees
Add the tactics used by BEC scammers to your security awareness training. As Business Email Compromise uses social engineering, your awareness training and simulated phishing exercises must reflect this complex aspect of BEC fraud. SafeTitan provides behavior-led security awareness training focusing on security behavior and staff reactions to social engineering.
Protect your M365 Environment.
As you read earlier in this article, Microsoft 365 is a targeted environment because it is popular and trusted. Also, a report has found that 90% of companies have security gaps in their M365 environment. Protecting this environment is essential, but intelligent measures must be taken as cybercriminals evolve their tactics. For example, QR code phishing is an evasive tactic that is increasingly used in BEC attacks. Conventional anti-phishing tools struggle to identify QR code phishing. The evasive and sophisticated techniques modern cybercriminals use are captured by advanced Integrated Cloud Email Security (ICES). Augmenting native M635 security with ICES anti-phishing technology, like PhishTitan, is essential in preventing BEC. The advanced offerings of PhishTitan include AI-driven threat intelligence, real-time threat analysis, and time-of-click protection. PhishTitan also deeply integrates with Office 365 email, protecting staff and C-Level executives.

Susan Morrow
- DATA PROTECTION
- EMAIL PHISING
- EMAIL SECURITY
Talk to our Team today


