
Cisco Umbrella Roaming Client- End-of-Life
Geraldine HuntThe imminent Cisco Umbrella Roaming Client End-of-Life has left many users uncertain about their next steps and exploring alternative DNS protection.
Millions of people are working from remote workspaces as a result of Covid-19. For most employees, this means working from home. When you expand the number of workspaces connected to your enterprise, you expand the attack surface, which means more real estate to secure and greater exposure to attacks. Because the majority of these users connect to the corporate network through VPN in order to access file shares, intranet applications and other resources, any malware infections obtained while at home can quickly spread throughout the enterprise.
The Covid-19 crisis has inflicted a great deal of disruption to most businesses. It is important to remember that cybercrime is a disruptive force as well. While company managers and internal IT work furiously to move and secure employee operations to home environments, hackers are embracing the new found opportunities that remote work represents for them. Besides having to deal with consumer level wireless bandwidth, kids’ home from school, barking dogs and countless interruptions, millions of employees that are adapting to the rigors of working from home must contend with another factor, hackers.
Most IT network professionals know how critical DNS is to any network. DNS is the master interpreter, the traffic cop that answers endless queries each day concerning websites, intranet sites, domain controllers and email services. Because DNS is so mission critical to the enterprise, it lies protected in its place behind the robust security of the perimeter. Unfortunately, users that work from home are dependent on consumer based routers now, most likely provided by their internet provider. Unlike internal IT, home users don’t think about securing their DNS router, if they even know what that is. This is why the attacks on consumer routers have spiked in the past month.
The attackers operate by using well-known exploits to hack into vulnerable devices and make changes to the router's DNS configuration, changes that most users won't notice.
To give you an idea of just how much the threat level against users has gone up, consider this. According to a leading VPN vendor, Google saw a 350 percent increase in phishing sites during the Coronavirus pandemic over the last 3 months. There were a total of 149,195 phishing sites in January, spiking to 522,495 in March. To also demonstrate how adaptable hackers are, more than 300,000 of these sites were contained some type of coronavirus theme.
Europol has issued warning concerning the sharp increase in not only phishing attacks, but DNS hijacking attacks as well. Cybersecurity Company, Bitdefender recently published a report showing new attack methods targeting consumer based routers began the third week of March. One such threat involves brute-force attacks with remote management credentials. Once compromised, the attackers then modify the DNS IP settings.
URLs that are popular right now such as aws.amazon.com, Disney.com and Washington.edu are then redirected. Users are then redirected to a Coronavirus-themed page that appears as if it is of the World Health Organization. A button is prominently displayed, allowing users to supposedly download the latest information and instructions concerning the COVID-19 virus. Upon clicking the button, a file is downloaded infecting the user’s machine with the Oski infostealer, a malware designed to steal browser passwords, cryptocurrency data and login credentials from the Windows registry and SWL databases.
One of the first steps users can do it to change the default credentials on their home router. Far too many users never change their default credentials. Users should also update their firmware and make sure it’s always up to date.
Besides user education, you can also expand the gamut of your security to match your newly enlarged enterprise. Companies that have relied on some type of appliance installed within the enterprise now must turn to security solutions that offer greater agility and scalability in order to meet the challenges of today. This means the cloud.
At TitanHQ, we have been creating cloud-based solutions to protect both on-premise and remote workspaces in equal fashion, years before the latest crisis at hand. Our SpamTitan email security solution includes tools such as double antivirus protection, data lost prevention and sandboxing. Our WebTitan DNS filtering solution blocks a multitude of threats including malware, phishing, viruses and ransomware from penetrating the browser sessions of your users. All of our solutions are rapidly scalable and can protect your users where ever it is they are working from, including BYOD environments.
DNS filtering should be an important component of your network security strategy used in conjunction with port monitoring, intrusion detection systems, web filtering software, intrusion prevention systems, antivirus, and firewalls. Together, these necessary layers work cohesively to create a functional and effective security protection system.
No system is of course bulletproof, and while it is true that cybercriminals are constantly changing domain names, solutions such as WebTitan DNS Filtering are highly effective in countering their cloaking efforts. WebTitan does this by categorizing an estimated 60,000-malware and spyware domains per day, tracking down dangerous sites and blocking them.
A schematic illustrating this process is shown below :
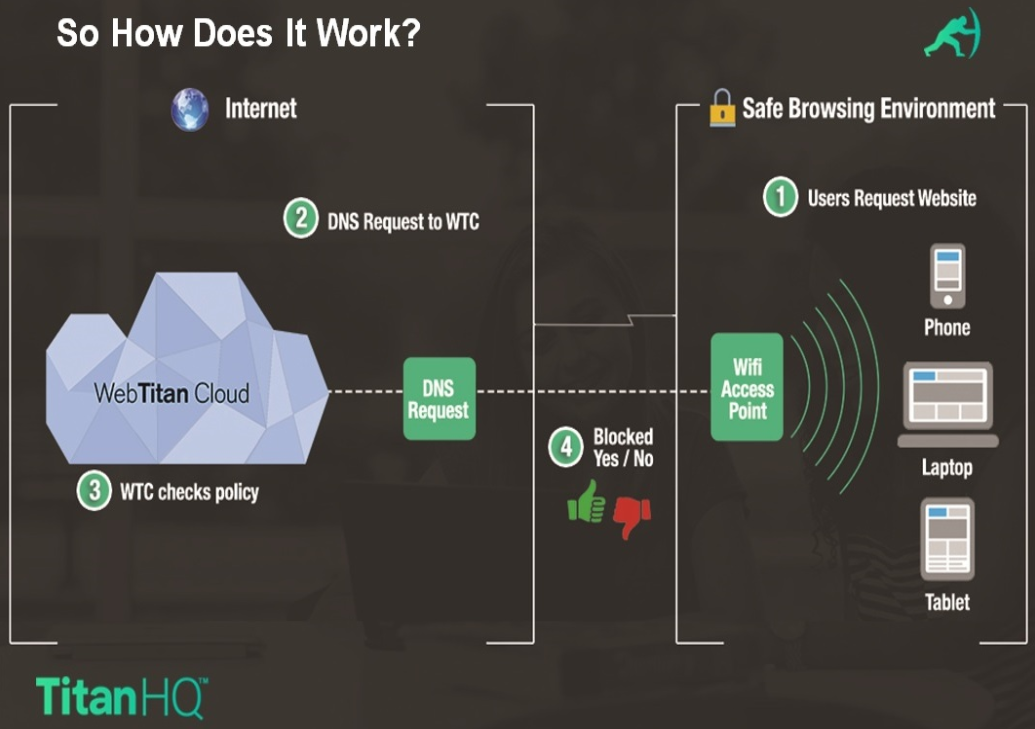
For any organization that takes network security seriously, the protection of their DNS infrastructure should be a vital part of their enterprise security plan. A little time and effort spent on DNS security can provide immediate and significant security benefits.

The imminent Cisco Umbrella Roaming Client End-of-Life has left many users uncertain about their next steps and exploring alternative DNS protection.

School districts around the world over are issuing Chromebooks to students to help close equity, technology and homework gaps. Discover why and how to protect K12 students.

A 2024 report highlights the soaring popularity of QR codes, with a 47% yearly usage surge. However, cybercriminals are exploiting this trend, targeting unsuspecting users with scams and malware infections due to...
Sign-up for email updates...
