
Cisco Umbrella Roaming Client- End-of-Life
Geraldine HuntThe imminent Cisco Umbrella Roaming Client End-of-Life has left many users uncertain about their next steps and exploring alternative DNS protection.
The Locky ransomware is distributed via spam email containing infected attachments and links to malicious websites. This new strain of ransomware is named after the file extension used when all your important files have been encrypted - .locky. As we move into the second quarter of 2016, ransomware distributed via invoice spam continues to dominate the IT security headlines. New strains appear all the time and their methods of infection are changing.
The latest headline-grabber, “Locky” attempts to scramble many of the files on all the drives it can find. This includes removable drives, network shares and mapped drives on Windows, Linux or MAC OSX. As with all ransomware, you can only unscramble them after you have paid up! Victims are invited to visit the dark-web and pay the crooks in bitcoins, after which the decryption key is provided.
So far, so similar. The difference here is the way the ransomware is distributed.
The main source of infection has been through spam email, many mostly disguised as invoices. The attachment is a Word document which contains the venerable old virus-carrier, the macro. This was the virus writers’ go-to method back in the late 1990s and, as such, had been consigned to history once Microsoft had pretty much disabled the auto-run function.
With Locky however, the recipient is asked to enable editing within the document, which allows the malware to run. And it has been pretty effective in persuading the innocent reader to click on the yellow “Enable Editing” button.
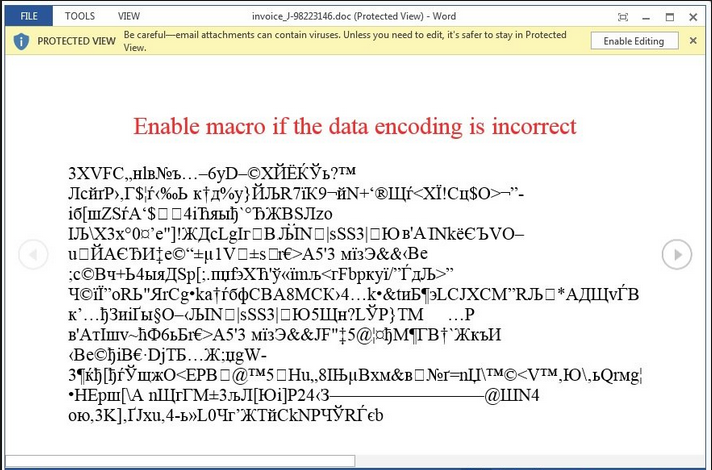
Once the macro runs, it downloads the ransomware, which then starts the task of encrypting all your precious files.
Reports suggest that the Locky spam email campaigns were well resourced and on a scale much larger than most. Many email messages had a subject that began “ATTN: Invoice…” or “Tracking documents”. The malware was spread very quickly, which caught out many anti-virus vendors and hit businesses that failed to have a policy of regular and frequent security updates.
They were greeted with this as their desktop:
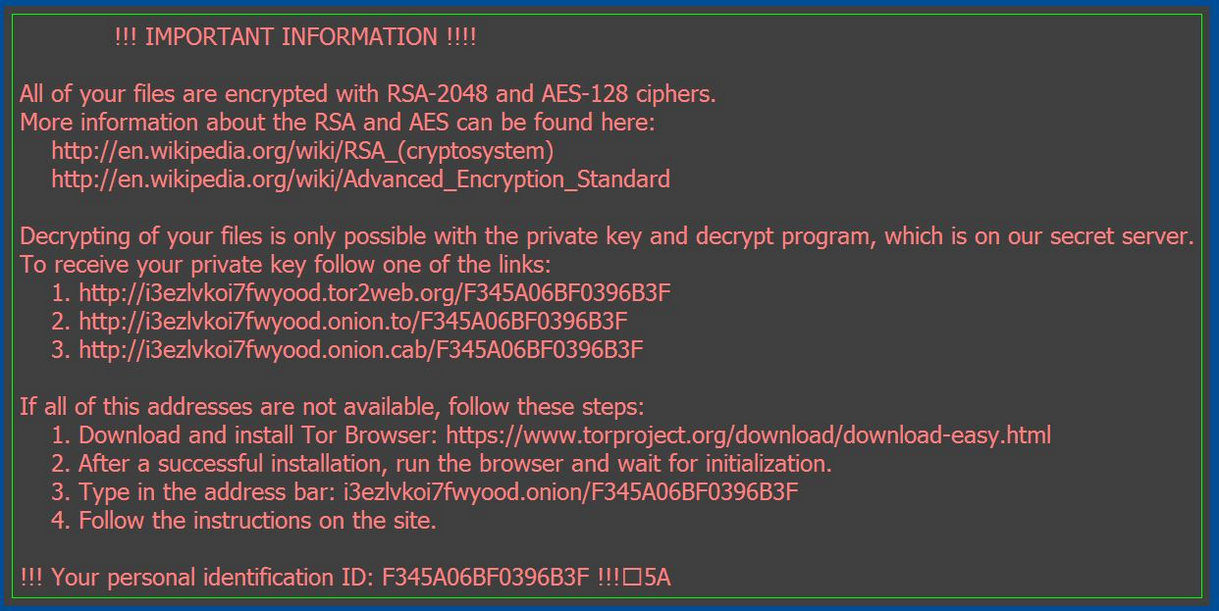
Despite its high profile, ransomware is just another type of malware; threatening your corporate data, reputation or bank balance.
A worrying trend is the increasingly convincing nature of the scams that criminals are using to persuade their victims to open malicious attachments or follow links to dubious websites. Despite all the information and warnings designed to make computer users suspicious of unexpected email, the cyber criminals are finding more and more successful ways to make their messages appear as legitimate and innocent as possible.
Spam campaigns now appear to be more localised: being based in the country or even region of the victim. Subjects are familiar and the message and attachment claim to be concerned with business processes and services that are common to the recipient. Couriers, utility companies, partner organisations and suppliers are all commonly used to dupe people into opening the document or clicking on the link. Even the most well-informed and well-intentioned person could be fooled.
This all means that simple anti-virus and an informed user-base is no longer enough to protect you and your data. Prevention is better than cure – especially when there is no cure without paying criminals!
You can no longer reply on one or two systems to save you from a determined attacker; it takes multiple systems to defend again the multiple ‘attack vectors’ that are being used. Let's take a look at what you need to put in place :
Backup
Your last-line of defence against ransomware. Off-site backups will save you in many disastrous situations, not just a malware attack. Use encrypted backups to keep your data secure.
Patching
Make sure your operating system and productivity software is kept up-to-date. Software updates will frequently include patches for newly discovered security vulnerabilities that could be exploited by attackers. Use internet-based updates or build in-house update systems to control updating.
Perform full third party application patching (in addition to OS patches). Some third party software such as Adobe Flash, is often targeted by malware and needs to be kept up-to-date.
Keep your security and anti-virus software up to date
Your anti-virus, anti spam and content filtering solutions are only as good as its latest update. You need to keep a regular and frequent update policy to protect yourself from the latest threats. Once a day is not enough!
Penetration tests
Perform regular network security assessments and penetration tests to discover unknown vulnerabilities.
Your Web Security Systems
Use a layered approach in order to protect your users and systems from malware.
Endpoint security software
Including client-based firewalls
If there's one thing to be said with certainty about ransomware attacks it's that recovering your data encrypted by the attack is next to impossible, so it is best to just properly protect yourself in the first place. The importance of backups in the battle against ransomware cannot be over emphasised. Backing up files to recover from a ransomware attack and ensuring the backup drive can’t be reached by malware is critical.

The imminent Cisco Umbrella Roaming Client End-of-Life has left many users uncertain about their next steps and exploring alternative DNS protection.

School districts around the world over are issuing Chromebooks to students to help close equity, technology and homework gaps. Discover why and how to protect K12 students.

A 2024 report highlights the soaring popularity of QR codes, with a 47% yearly usage surge. However, cybercriminals are exploiting this trend, targeting unsuspecting users with scams and malware infections due to...
Sign-up for email updates...
